Manuscript accepted on :November 15, 2017
Published online on: --
B. Kiran Bala1 and A. Bala Kumar2
and A. Bala Kumar2
1Department of Computer Science and Engineering, K.Ramakrishnan College of Engineering, Trichy, Tamil Nadu, India-621112.
2Department of Electronics andCommunication Engineering, K.Ramakrishnan College of Engineering, Trichy, Tamil Nadu, India-621112.
Corresponding Author E-mail: kiranit2010@gmail.com
DOI : https://dx.doi.org/10.13005/bpj/1294
Abstract
To give more security for the biomedical images for the patient betterment as well privacy for the patient highly confidently patient image report can be placed in database. If unknown persons like hospital staffs, relatives and third parties like intruder trying to see the report it has in the form of hidden state in another image. The patient detail like MRI image has been converted into any form of steganography. Then, encrypt those images by using proposed cryptography algorithm and place in the database.
Keywords
Authentication Cryptography; Mammogram Image; Steganography;
Download this article as:| Copy the following to cite this article: Bala B. K, Kumar A. B. The Combination of Steganography and Cryptography for Medical Image Applications. Biomed Pharmacol J 2017;10(4). |
| Copy the following to cite this URL: Bala B. K, Kumar A. B. The Combination of Steganography and Cryptography for Medical Image Applications. Biomed Pharmacol J 2017;10(4). Available from: http://biomedpharmajournal.org/?p=17791 |
Introduction
The security is the very big issue in present technology to overcome those issue in various field day by day so many new proposed technique is released every day but in the field of medical the security is very much important to give privacy and security for the patient details to avoid data hacking and data surfing in the hospital database even though hospital staff should not directly see the without permission of patient as well as doctor. The Proposed system deals with the MRI scan image for the patient and it should be pre-processed and then convert into steganography technique it is in the form of two things first one is in image form another type is in form of text form each time MRI image has been converted into text or image form.4-5
The next step for the proposed system is from that using the proposed cryptography algorithm just convert those unknown form into another form for the purpose of security aspect to give privacy and authentication for the patient as well as hospital for high quality of service. MIAS database is used for the proposed system from that database the entire process has been carried out for the better result for the present technology result. The proposed system is not deals with the diagnosis of the disease from the image but the system is mainly focus on the security aspect of the system.2,3 Partitioning and segment the sample image is also a process of technique to calculate and hide the data in the sample stego-image is possible.8,9
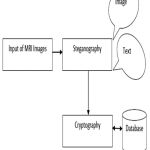 |
Figure 1: Basic Diagram for proposed system
|
The proposed system is having two modules namely steganography form and cryptography module from the input image random chosen of image or text from the proposed system and then by using image conversion means MRI image has been converted into binary form and then plain image from the proposed algorithm identify the unused space from the plain image insert the MRI image into the plain image and now the MRI image is in unknown form and then encrypt the image into cipher text and store in the database. Likewise, if MRI image can also be convert into text and encrypt into cipher text and finally store into database.6
Methodologies and Results
Initial Process for Image
The First and foremost process in the proposed system after getting the MRI image the system will random conversion of image or text from of the MRI image.3
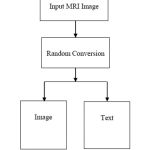 |
Figure 2: Random Conversion for steganography process
|
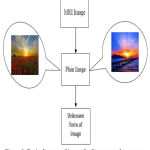 |
Figure 3: Basic diagram of image for Steganography process
|
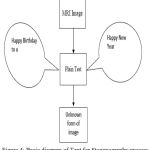 |
Figure 4: Basic diagram of Text for Steganography process
|
The figure 3 & figure 4 for the process of steganography has been shown in the figures and finally store in the database of the proposed system.1 In addition to that partition and segment can be made for the better result in order to give efficient result like to avoid FAR and FRR.8
Results and Discussion
The Proposed system has implementation of the entire process and which has process and execution time, accuracy, FAR and FRR has been discussed in the system.8
Table 1: Implementation Result of Proposed system in time wise
| Image Type | Time (in sec) |
| JPEG | 0.001 |
| MPEG | 0.001 |
| BMP | 0.002 |
| PNG | 0.001 |
| GIF | 0.001 |
| PNM | 0.001 |
| BAT | 0.003 |
| BPG | 0.001 |
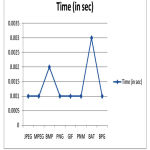 |
Figure 5: Graph for Image type & time taken for conversion
|
Table 2: Implementation Result of Proposed system in accuracy wise
| Image Type | Accuracy (in %) |
| JPEG | 99.3 |
| MPEG | 99.4 |
| BMP | 99.5 |
| PNG | 99.5 |
| GIF | 99.4 |
| PNM | 99.5 |
| BAT | 99.3 |
| BPG | 99.4 |
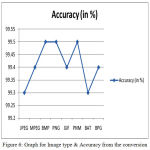 |
Figure 6: Graph for Image type & Accuracy from the conversion
|
Table 3: Implementation Result of Proposed system in FAR wise
| Image Type | FAR (in %) |
| JPEG | 99.7 |
| MPEG | 99.1 |
| BMP | 99.2 |
| PNG | 98.8 |
| GIF | 99.9 |
| PNM | 99.1 |
| BAT | 99.3 |
| BPG | 99.5 |
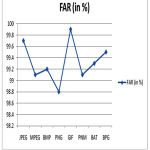 |
Figure 7: Graph for Image type & FAR from the conversion
|
Table 4: Implementation Result of Proposed system in FRR wise
| Image Type | FRR (in %) |
| JPEG | 99.4 |
| MPEG | 99.1 |
| BMP | 99.2 |
| PNG | 99.1 |
| GIF | 99.5 |
| PNM | 99.3 |
| BAT | 99.2 |
| BPG | 99.1 |
From the implementation part the discussion has been made that the input image converted and result as well as graphs are available in the figure 5, figure 6, figure 7 & figure 8 for the proposed system.
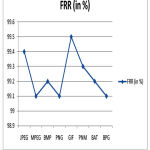 |
Figure 8: Graph for Image type & FRR from the conversion
|
Conclusion
The experimental results reported in this paper shown in the figure 5 & figure 6 for the processing and efficiency of the entire proposed system is possible the justification shown in the implementation part is available. The proposed system deals with security of the present technology and which gives the input for the issues in the present system and solution to the issues of the present technology for the biomedical application for the medical sector for privacy and highly confidentially data of the patient.
References
- Kiran B.B. A Novel Approach to Generate a Key for Cryptographic Algorithm. Journal of Chemical and Pharmaceutical Sciences, Special. 2017 February;2:229-231.
CrossRef - Kiran B.B. A Novel Approach to Identify the Micro calcification Images. Journal of Chemical and Pharmaceutical Sciences, Special. 2017 February;2:190-192.
CrossRef - Kiran B.B. Biometrics for Mobile Banking. International Journal of Technology and Engineering System. 2011;2(1):95-97.
- http://www. mammoimage. Org / databases/
- Kiran B.B, Sasikumar R. Identification Of Cancer From The Mammogram Images By Using Frequency Domain Approaches.International Journal of ChemTech Research. 2017 April;10:5.
- Kiran B.B, nithya T.m. Remedy For Disease Affected Iris In Iris Recognition. International Journal of Research in Engineering and Technology. ISSN: 2319–1163, 2012;332-334.
- Kiran B.B, Lourdu J. Multimodal Biometrics using Cryptographic Algorithm. European Journal of dAcaemic Essays. 2014;6-10.
- Yand K, Ramaniah G.V A Novel Method Avoids the Fall-Off Boundaries by Using Try-Way Pixel Value Difference and Modulus Function in Image Steganography. International journal of computer science and Mechatronics. 2015;1(1 ):7-11.
- Kakade R, Kasar N, Kulkarni S, Kumbalpuri S, Patil S. Image Steganography and Data hiding in QR Code. International Research Journal of Engineering and Technology. 2017;4(5):2926-2928.







